Why Identity & Access Management Matters?
Stolen credentials accounted for 22% of initial breach incidents in 2024, making credential theft the most common entry vector for attackers.
Without adaptive authentication and least-privilege controls, every account becomes a potential breach path.


Only 46% of organizations rate their IAM controls as effective
Widespread deficiencies in lifecycle management, session visibility, and policy portability leave access permissions outdated and vulnerable.
Key IAM services we provide
Privileged Access Management (PAM)
Secure, control, and monitor privileged accounts to prevent misuse, detect anomalies, and meet regulatory requirements-all while maintaining user efficiency.
Single Sign-On (SSO)
Enable users to access multiple enterprise applications securely with a single login, enhancing usability without compromising security.
Multi-Factor Authentication (MFA)
Add layers of protection at login using methods such as one-time passcodes or biometrics to neutralize credential-based attacks.
Identity Lifecycle Management (ILM)
Automate user onboarding, role changes, and deprovisioning to ensure that access rights remain current and reduces orphaned or excessive privileges.
Identity Governance & Administration (IGA)
Centralize visibility and control over user permissions-including attestations and policy enforcement—to prevent inappropriate access and ensure compliance.
Zero‑Trust Enforcement
Implement continuous verification for every user, device, and session-embracing the principle of “never trust, always verify” to reduce attack surfaces and enforce least privilege across cloud and on-prem systems.







IAM Compliance Enablement
for Saudi Laws & Frameworks



Ahlan Cyber embeds compliance into every IAM stage-assessment, deployment, governance, and monitoring-meeting Saudi regulatory and sector requirements.
With automated governance, AI-driven risk analytics, and audit-ready trails, we turn compliance into a strategic advantage while establishing a Zero Trust foundation.











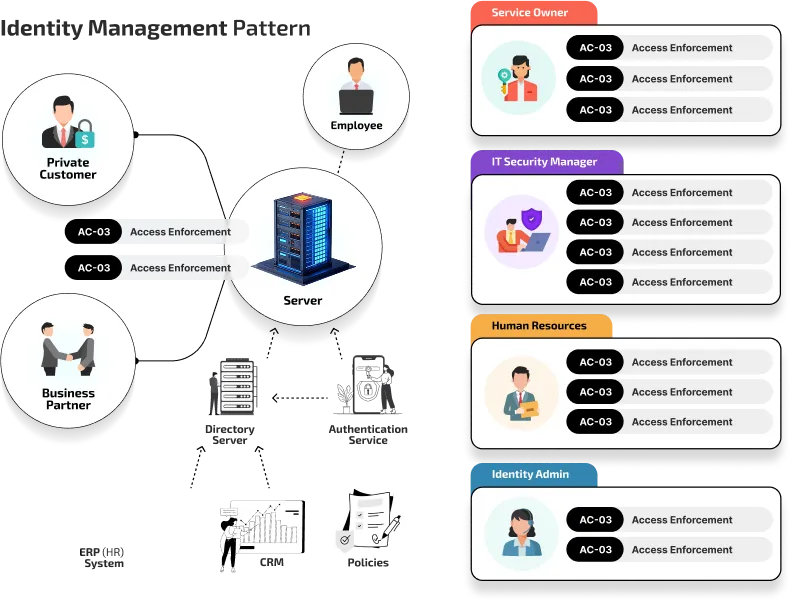
Modern IAM Architecture
Why Choose Ahlan Cyber
for Identity Access Management?

Regional Expertise & Strategic Alignment
Saudi-born with deep understanding of local priorities and the Nafath ecosystem, we tailor IAM solutions to meet regional standards.

Dedicated IAM Practice
A dedicated team of certified IAM professionals delivers system design, deployment, and ongoing governance for identity-first security.

End-to-End IAM Lifecycle
From discovery and risk assessment to deployment, fraud detection (ITDR), behavioral monitoring, and lifecycle governance (ILM/IGA), we deliver a comprehensive IAM program, not just point solutions.

Adaptive & Zero-Trust Centric
Built on “never trust, always verify,” our IAM frameworks feature adaptive authentication, dynamic access, and ECC/PDPL-aligned validation.

Compliance Embedded & Auditable
Compliance is built-in with automated PDPL consent, audit trails, privileged access reporting, and workflows that support audit readiness.

Case Studies
Recent Case Studies

Q&A
Frequently Asked Questions
Yes. Modern IAM solutions support seamless integration with cloud environments—whether Azure, AWS, Google Cloud, or SaaS apps—using federation standards like SAML, OAuth2, and OpenID Connect. They also offer support for BYOD and remote device authentication, helping organizations manage secure access across hybrid networks.
MFA (Multi‑Factor Authentication) verifies users at login using multiple factors (e.g. SMS, biometrics), preventing credential-based breaches. SSO (Single Sign-On) streamlines login by allowing one set of credentials to access multiple applications, enhancing both usability and security posture. PAM (Privileged Access Management) focuses on accounts with elevated privileges, controlling who can access sensitive systems, managing credential vaults, tracking sessions, and enforcing least-privilege principles.
Ahlan Cyber’s IAM frameworks embed compliance with PDPL and Saudi regulations (NCA ECC, SAMA, etc.)—enabling automated consent logging, audit trail generation, and privilege attestation. We also support IAM-focused audits, including PDPL readiness assessments and report preparation, to help clients meet regulatory mandates effectively.
IAM enhances cybersecurity and operational efficiency by providing unified access control, strengthened authentication, automated user provisioning, and audit-ready reporting. In fact,
85% of organizations adopting IAM in the Middle East report a 30% reduction in security incidents, showing sustained operational gains and compliance confidence .

Get in Touch
3141, Anas Bin Malik Street,
8292 Al Malqa, Riyadh,
Kingdom of Saudi Arabia.
 +98497 55979
+98497 55979

